The 8 Design Principles Behind Azure Landing Zones + Hands-On Guide
Everything you need to know about designing enterprise-ready Azure environments.
Moving to Azure isn’t just about lifting and shifting workloads. The real challenge is building a foundation that balances speed, governance, and security. That’s where Azure Landing Zones come in.
Landing zones are the backbone of an enterprise-ready Azure environment. They give teams freedom to innovate while ensuring that governance, compliance, and operational standards are baked in.
But here’s the catch: not all landing zones are equal. To get them right, you need to follow eight design principles. These principles provide the blueprint for scaling Azure in a way that works for both IT and the business.
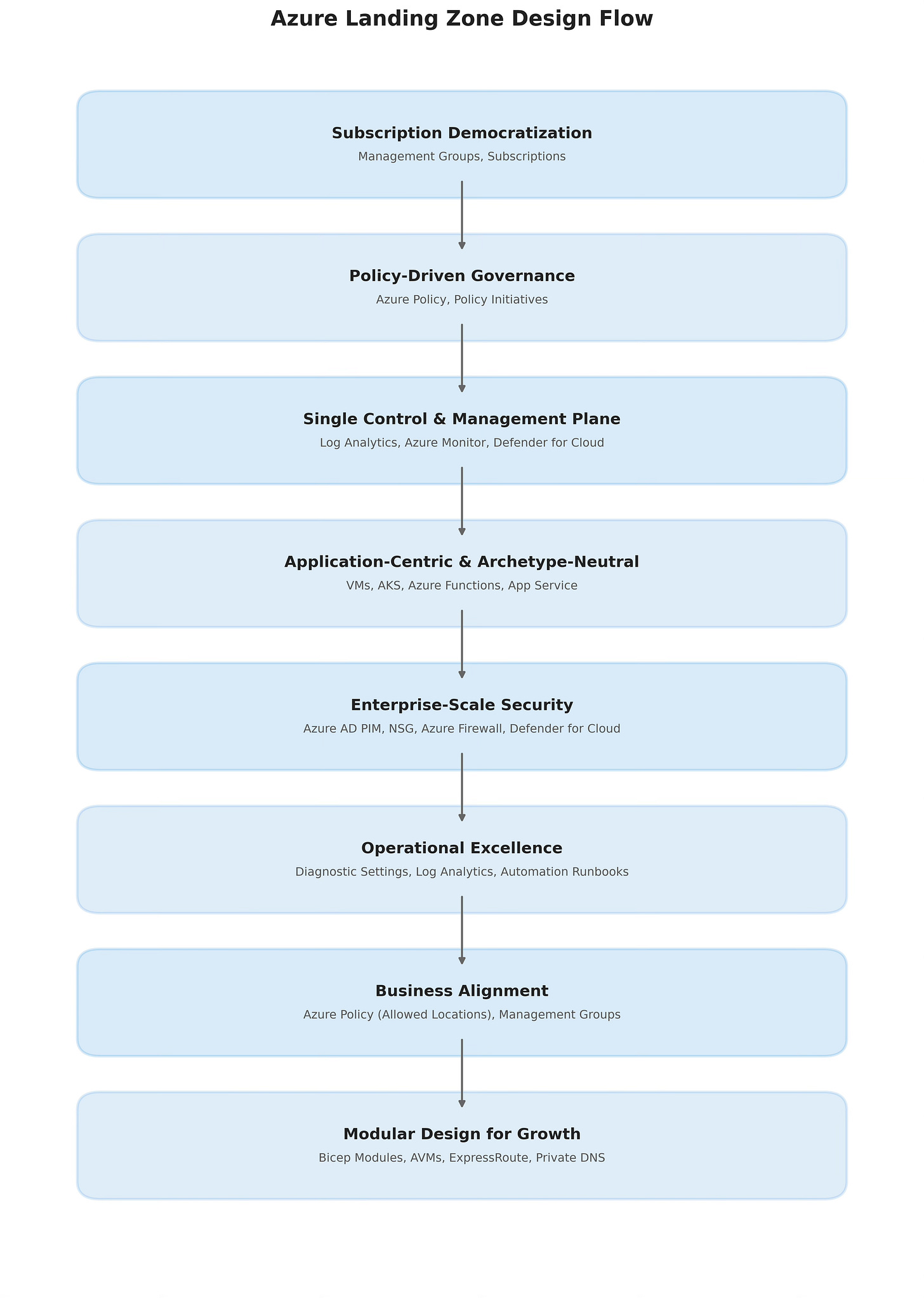
1. Subscription Democratization
Principle: Subscriptions should be the unit of scale, management, and isolation.
In practice: Instead of putting all workloads into one subscription, each product team gets its own. Teams move fast, while governance is applied centrally through management groups.
2. Policy-Driven Governance
Principle: Governance must be automated, not manual.
In practice: Azure Policies enforce tagging rules such as CostCenter and Environment. Developers can deploy at speed, but compliance and cost tracking are guaranteed.
3. Single Control and Management Plane
Principle: Operations need one consistent place to manage resources.
In practice: Logs from AKS, VMs, and SQL are centralized into a single Log Analytics workspace. Operations teams monitor everything in Azure Monitor—no more jumping between tools.
4. Application-Centric and Archetype-Neutral
Principle: Landing zones should support all app types, old and new.
In practice: A legacy Windows app runs on VMs, while another team builds on AKS and another uses Azure Functions. The landing zone supports all of them without extra redesign.
5. Align with Enterprise-Scale Security
Principle: Security must be built in from the start.
In practice: Administrators use Privileged Identity Management for just-in-time access. NSGs and Azure Firewall secure the network. Defender for Cloud enforces enterprise security controls.
6. Enable Operational Excellence
Principle: Operations should scale with automation.
In practice: New VMs or AKS clusters are deployed with diagnostic settings enabled automatically. Logs flow into Log Analytics, and automation runbooks restart unhealthy resources without waiting for a human.
7. Align to Business Requirements
Principle: The cloud foundation should reflect real-world business needs.
In practice: A healthcare company enforces policies so resources can only be deployed in U.S. regions like East US and Central US to stay HIPAA compliant.
8. Modular Design for Growth
Principle: Build small today, expand tomorrow.
In practice: Start with networking and identity. Later, add modules for Azure Firewall, Private DNS, and ExpressRoute. Each is reusable and deployed through Bicep templates or Azure Verified Modules.
Hands-On Guide: Build a Policy-Driven Landing Zone
To make this real, here’s a simple workshop you can run in your own Azure environment. It demonstrates three principles: subscription democratization, policy-driven governance, and operational excellence.
Scenario
You need a landing zone for a dev team. They should deploy freely, but governance and monitoring must be applied automatically.
Step 1: Create a Management Group
az account management-group create --name DevTeam-MG --display-name "Dev Team Management Group"Step 2: Assign a Subscription
az account management-group subscription add \
--name DevTeam-MG \
--subscription <SubscriptionID>Step 3: Apply a Tagging Policy
az policy assignment create \
--name "enforce-tags" \
--scope "/providers/Microsoft.Management/managementGroups/DevTeam-MG" \
--policy "/providers/Microsoft.Authorization/policyDefinitions/require-tag-costCenter" \
--params '{"tagName":{"value":"CostCenter"}}'Step 4: Enable Centralized Monitoring
az monitor diagnostic-settings create \
--name "send-to-central-logs" \
--resource-group <RGName> \
--workspace <LogAnalyticsID>Step 5: Test It
Deploy a VM without tags. The policy should block the deployment or require you to tag it. Logs should automatically flow into Log Analytics.
Outcome: You’ve now created a lightweight landing zone that enforces governance and monitoring without slowing down developers.
Azure Landing Zones are more than templates, they’re the framework for scaling cloud adoption. By following these eight principles, you’ll build an environment that’s secure, compliant, and aligned with business goals.
Start small. Run the workshop above. Then expand with modular components as your organization grows. The best landing zones aren’t built once, they evolve with you.